In the ever-advancing modern world, cybercriminals are leading adversaries for businesses of all sizes and industries. As fearmongering as it may sound, no one is safe from cyber attacks.
Hacked devices, crashed websites, breached networks, stolen credit card data, and other incidents have become far too common in the workplace. And hackers are constantly coming up with new ways to exploit vulnerabilities.
As business owners and gatekeepers of your client and employees’ personal information, vigilance is necessary.
These breaches can cost you thousands to millions of dollars in stolen assets, lost work time, and repair costs. It can seriously damage your business’s reputation.
Cyber attacks aren’t going away anytime soon. And while there isn’t a definite way to prevent ALL malicious attacks, with the proper technology and knowledge, you can significantly reduce the risk.
Scams, Hacks, and Downloads
To understand how these types of cyber attacks work, think of them in three separate categories – scams, hacks, and downloads.
- Scams are attacks where the cybercriminal directly interacts with the target, primarily via email or phone. The criminal convinces their victim to “voluntarily” give up their information or funds.
- Hacks occur when a cyber-criminal uses their computer and programming skills to find and exploit weaknesses in a company’s security system.
- Downloads are a part of a malicious program which silently implants itself in a user’s system when that individual visits an infected website or clicks infected links.
With these cyber attack categories in mind, let’s explore further.
Malware
Malware, short for malicious software, is created with the intent to harm a user’s data and/or device. You may have heard of different types of malware, including viruses, worms, and trojans. These types of malware can infect in a variety of ways. Viruses, for example, spread uncontrollably by attaching themselves to clean files to infect other clean files.
The end result damages a system’s core functionality and deleting or corrupting files.
How to Prevent Malware
There are two main ways of preventing malware from damaging your system – prevention and awareness. So, consider:
- Up-to-date security policy.
- Up-to-date antivirus.
- Making sure that your device’s security and antivirus are up to date and functional is critical for a continuity plan.
- Always prepare for attacks.
- Don’t download files from suspicious or unknown senders.
Ransomware
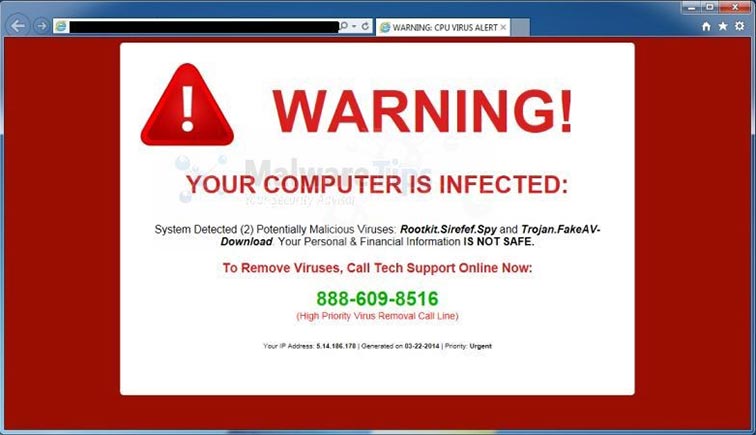
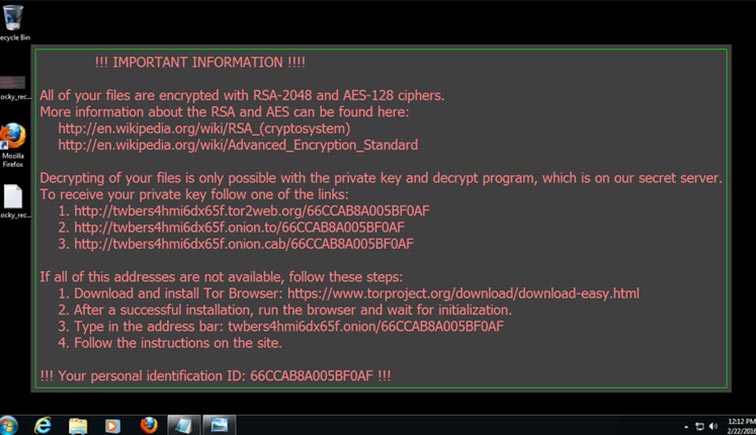
Ransomware is a cyber attack that’s infamous and extremely dangerous. This type of attack can function like Malware, or it can be a hack.
Ransomware attacks, like Cryptolocker, typically have a pattern they follow: the hacker breaches the system and installs a malicious program. Once this program downloads, it silently spreads through the local network and locks down all the connected devices. The program will display a ransom message demanding money to unlock the device. If you don’t pay by a certain time, the attack will destroy the data.
These attacks happen to businesses of all kinds, including costing a hospital a $10 million fine.
How to Prevent Ransomware Attacks
Pre-emptively stopping Ransomware is no easy task, and rooting it out after an attack is impossible. The most important methods of protection are again, awareness and security.
- Antivirus and firewalls are should always be up to date.
- Avoid untrustworthy parts of the internet.
- Treat strange links and web pages as though they can destroy your business and cost you millions of dollars – because they can.
Remote Access Attacks
A Remote Access cyber attack, also known as a remote exploit, can target one device or an entire network. Android phones were a recent target of the remote hacking attack, RAMpage, exposing vulnerabilities in the device’s RAM chips.
The attacker finds vulnerable points in a network’s security software to access the device or system. Once this code installs, it reaches out to another computer and downloads the rest of a malicious code.
Remote control attacks can view or steal data illegally and introduce viruses or other malicious software into the system.
How to Prevent Remote Access Attacks
Remote takeover’s impact is far-reaching. But there are ways you can protect yourself.
- Strengthen passwords for devices – use a mix of numbers, letters, and special characters.
- Implement security software that automatically updates and runs a periodic “deep scan” to search for viruses and malware.
- Review any software that employees use to remotely access the network, and disable it until needed.
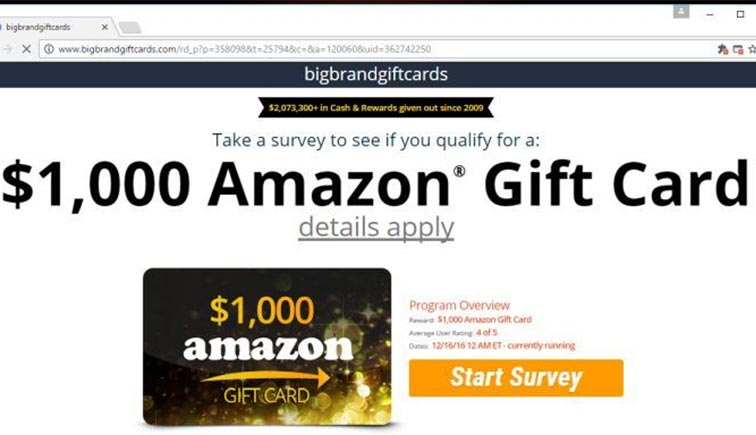
Malvertising – Malicious Advertising
You know those ads that promise to cure weight loss or highlight celebrity scandals?
In the cyber world, this is known as Malicious Advertising. Cyber criminals use website ads to lure people into clicking on these advertisements to download malicious software onto their computers without detection until it’s too late.
How to Prevent Malicious Advertising Attacks
While there’s never a one size fits all solution, here are a few things you can do.
- Use an ad blocker to block all advertisements from displaying on websites you visit.
- Don’t click on ads, especially if it’s “too good to be true.”
- Search for a company’s website and reviews to see if the source is legitimate.
Phishing
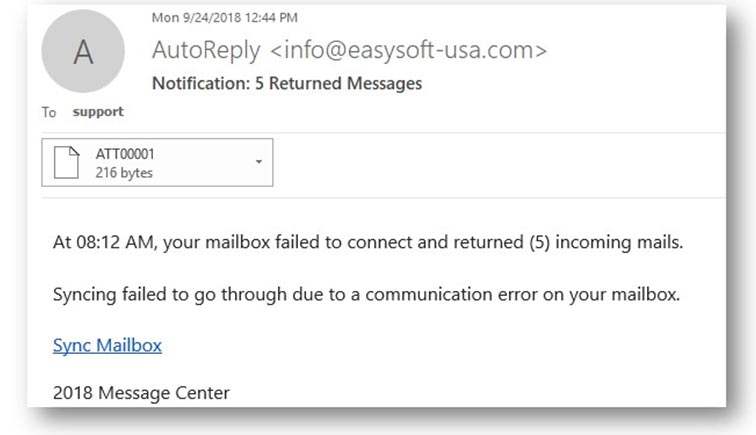
Phishing – everyone has experienced it at some point. It could be an email in your inbox disguised as sent from a friend or trusted company.
Hackers will use familiar names or the name of large businesses to try and steal personal information and data. The email is often convincing, even appearing to come from the company itself. Typically, phishing scams will include a link in their email, asking for you to perform an action, like in the example above.
Phishing emails are tricky. While you may not be able to prevent yourself from receiving one, you can learn how to spot one.
How to Prevent Phishing Emails
While there’s no single fool-proof way to avoid phishing scams, there are some guidelines you can follow:
- Never give out your personal information.
- Frequently check your online accounts.
- Use anti-virus software and a managed firewall.
- Train employees and keep informed about the latest attacks.
Password Theft

Surprisingly, 65% of business managers record their password on a paper or share it with other individuals.
But for cyber criminals, access to these passwords can have a profound affect, allowing them to infiltrate a network and gain excess to personal data including client and employee information.
There are three ways hackers can go about stealing password information:
- Brute Force Attack: using a program to try and log in with password combinations.
- Dictionary Attack: using a program or script to try to login by cycling through combinations of common words found in the dictionary.
- Key Logger Attack: uses a program to track a user’s keystrokes, so they can see exactly how you type on the keyboard.
How to Prevent Password Theft
A password is nothing unless it’s strong. The stronger your password, the safer your account.
Your passwords should be:
- Long, strong and complex, using number, letters, and special characters.
- Not easy to guess.
- Use two-factor authentication, like a code sent to your phone for an extra layer of security.
- Use a different password for every account.
- Changed frequently; shoot for every 3 months.
Denial of Service (DoS)

A denial-of-service (DoS) is any type of attack where the attackers try to prevent users from accessing the service. In a DoS attack, it makes it impossible for network users to access information or services by flooding the network with requests that tie up its resources.
How to Prevent DoS Attacks
Unfortunately, you can’t prevent a DoS attack. But you can reduce the chance of having your computer be a pawn.
- Restrict bandwidth usage to authenticated users only by deploying an antivirus program and a managed firewall in your network.
- Continually assess and check your server configuration.
- Consult a specialist who can offer guidance and protection against DoS attacks.
Man In The Middle

A Man in the Middle (MITM) attack occurs when a hacker intercepts communication between two systems. It can happen in any form of online communication, including email, websites, and networks.
This happens when communications over the internet do not occur over a secure connection. For example, websites with “https” before their URL use an internet protocol policy that prevents hackers from eavesdropping on this information.
How to Prevent Middle Man Attacks
While MITM attacks are an advanced form of cyber-criminal activity, you can try safeguarding your organization by using:
- Encrypted email, which ensures only intended recipients can read them and leaves no room for hackers to alter your messages.
- Certificate-Based Authentication for all employee machines and devices, only endpoints with properly configured certificates can access the systems and networks.
What’s in Your Cyber Attack Response Plan?
When it comes to cyber attacks, there is no silver bullet. You’ll never be sure when or how the next incident happens. But avoiding a costly crisis comes down to how you manage an attack before, during, and after it happens.
Consider these 3 key areas to a cyber attack response plan:
- Preparation: A well-prepared team is essential for dealing with a cyber attack. A 24/7 monitoring solution can provide early warnings of cyber-attacks.
- Response: In just minutes, your entire network can be destroyed. Coordinate with your team to develop a response plan to mitigate the risks of downtime and costs.
- Recovery: Every crisis creates opportunities for an organization to respond effectively and to find areas of improvement.
Ready to Take Cybersecurity Seriously?
As long as the internet exists, cyber attacks will continue to be an ongoing threat.
As a business owner, you may not have the resources and response capabilities to mitigate these risks. But with a Managed Service Provider like Strategy, our team of professionals can provide much needed external support in monitoring and maintaining your infrastructure while implementing a proactive risk management solution.
If you’re interested in learning more about safeguarding your business, get in touch with one of our Tech Specialists today.